All You Must Know About SSL Encryption Techniques
The penetration of the internet has also led to an increase in the number of incidents of data breaches. Data breaches can lead to severe repercussions for businesses. There could be severe penalties from governments, lawsuits, and loss of customer trust. A report from IBM states that the average cost of a data breach is around US$ 3.86 million in 2020.
In light of this, it becomes necessary for businesses to have proper systems to prevent this from happening. Encryption is a crucial element in ensuring the security of the networks and the website. It helps companies to thwart off data breaches. This article will discuss various SSL encryption techniques and how it helps businesses by preventing data breaches.
The Basic Concept of SSL nd SSL Certificates
One of the automatic choices for businesses when dealing with encryption is installing an SSL certificate. But let us first understand more about SSL technology. The secure socket layer allows web servers and web clients to communicate safely. It helps to create connections that cannot be easily broken into by a third-party.
Currently, SSL certificates use the Transport layer Security (TLS) technology, and the communication is encrypted so that it is readable only by the desired recipient. The certificates also authenticate the recipient of the information and ensure you are not interacting with an impostor. Businesses can have a robust security process if they choose an SSL certificate from Genuine SSL Providers like ClickSSL because they not only give trusted SSL Certificates but also provide you huge amount of CA Warranty as a security.
SSL certificates also engender a sense of trust in website visitors’ minds by checking the padlock sign’s presence on the address bar. Moreover, e-commerce sites must adhere to the PCI-DSS norms that require you to install an SSL certificate. It can also prevent phishing attacks as criminals will find it difficult to procure the certificate through false credentials.
Basics Of Encryption With Types
The algorithms used in the encryption process also use cryptographic keys that ensure that the process is complete. There are two main types of encryption, viz. symmetric and asymmetric encryption. They use different algorithms to encrypt data.
1 :Symmetric encryption
This form of encryption uses the same key to encrypt as well as to decrypt data. It is more of a straightforward process of encryption. One of its critical features is its simplicity, but the data cannot be understood by anyone who does not possess the decryption key. It can be a passcode or a string of letters that was created through a number generator.
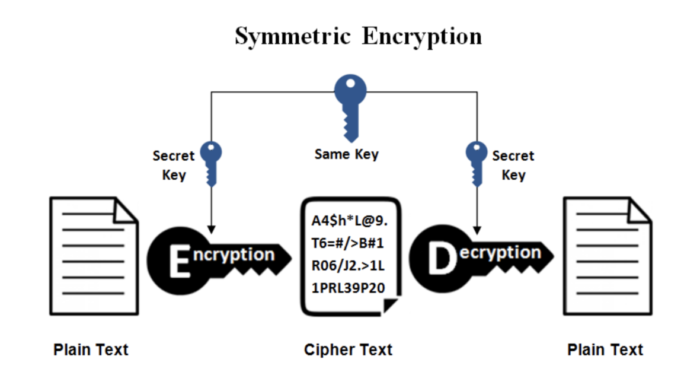
They are faster than asymmetric encryption and require lesser computational power, and do not reduce internet speed. There are several symmetric encryption techniques in place, but we will discuss some of the common ones.
2 :DES Encryption Algorithm
This encryption method used a 56-bit encryption key and was used in the TLS versions 1.0 and 1.1. The algorithm converts 64 bits of data by dividing it into two blocks, each of 32 bits. The encryption process is then done individually.
There are 16 rounds of processes like permutation, expansion, substitution, or XOR, along with a round key. The length of the encryption key was low that allowed brute force attacks against its networks. The DES algorithm was risky and had been breached by several entities. It is currently not in use.
3 :3DES Encryption Algorithm
It is officially known as the triple Data Encryption algorithm and is usually known as 3DES. 3DES is an upgraded version of DES and uses the DES algorithm thrice for each block of data. This algorithm also found usage in various cryptographic protocols like IPsec, TLS, OpenVPN, and SSH.
The algorithm was used in various applications, including the EMV payment system, Firefox, and Microsoft Office. The Sweet32 vulnerability was a critical one, and the National Institute of Standards and Technology (NIST) announced guidance that discontinued the usage of the algorithm after 2023.
4 :AES Encryption Algorithm
The NIST approved the encryption standard in 2001. It is widely adopted and is faster than the DES technique. Some of this algorithm’s critical features are the use of 128-bit data and 128/ 192/256-bit keys. It has a series of linked operations and is based on substitution and permutation.
In this process, the data is transformed into blocks, and then an encryption key is used to encrypt the data. Several sub-processes involve sub-bytes, shift rows, mix columns, and add round keys. The decryption of the ciphertext involves these activities in reverse order. AES has several uses, including processor security, wireless security, encrypting mobile apps, VPNs, wi-fi security, etc.
5 :Asymmetric Encryption
The asymmetric encryption method uses two distinct but related keys. The public key is used for encryption, while the private key is used for decryption. The private key is kept a secret, with only the designated recipient being able to use it to decrypt the message.
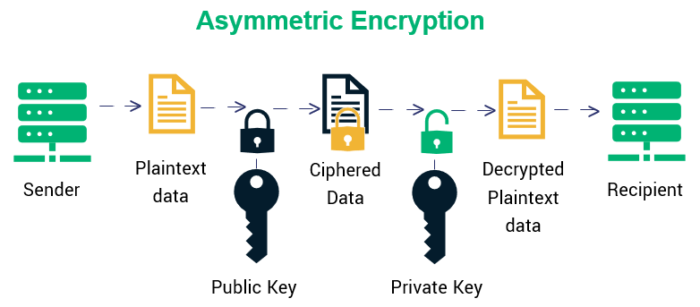
Your data is protected against any man-in-the-middle attacks and allows you to create a safe connection without the entities needing to exchange keys beforehand. The algorithm uses a key-generating protocol that generates a pair of keys. An encryption function helps encrypt the data, and the decryption function allows decryption of the data by the intended recipient of the data.
6 :RSA Encryption Algorithm
The RSA algorithm is among the most widely used asymmetric algorithms and uses the prime factorization method. The method uses two big prime numbers that are then multiplied to a more significant number. The two original numbers must be determined from this huge number. Cracking it isn’t easy, and studies show that it could take years to do so.
RSA provides scalability and is available in various bit lengths, viz. 768-bit, 1024-bit, 2048-bit, 4096-bit, etc. it uses a simple approach that makes its use in PKI easier. This encryption method is widely used in SSL technology.
7:ECC Encryption Algorithm
This encryption method involves an elliptic curve, and the set of points satisfy a mathematical equation (y2 = x3 + ax + b). It is a complex algorithm and is irreversible, which means that it is difficult to be reversed and return to the original point. It becomes challenging to find a new point even if the original point is known.
As it is more complex, this method offers greater protection levels. The shorter keys allow the algorithm to run faster and require lesser computing power. If it is used in SSL certificates, the website loads faster. This method is used to apply digital signatures and in pseudo-random generators.
How SSL certificates Work
When a browser tries to connect to a website, it requests the website for identification. The web server sends a copy of the SSL certificate. It is checked whether the certificate can be trusted. If it is from a trusted CA, a message is sent back to the server. The server reverts with a digitally signed acknowledgment, and encrypted data can be shared between the web server and the browser.
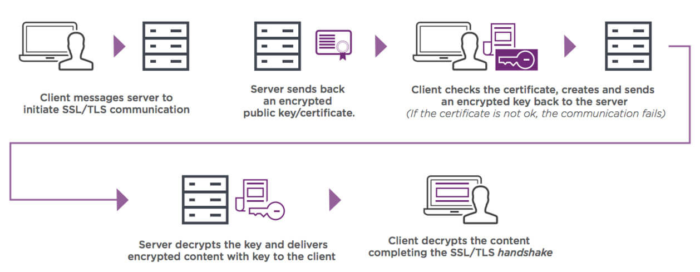
There are various types of certificates, and you can choose one based on your requirement. Blogs and smaller websites can choose a single-domain SSL certificate. If you wish to secure several domains and multiple sub-domains together, one of the Multi Domain SSL certificatescan help and a single Wildcard SSL certificate is the perfect solution where the web store is occupied with sub-domains and wishes to encrypt all information that is transmitted over the main domain and its related sub-domains.
Conclusion
The increase in the number of successful data breaches has led businesses to secure their internal processes. One of the best ways is to use SSL encryption to ensure that the communication between the server and the browser clients is secure. It will prevent any unauthorized third-party from accessing the information.






You must be logged in to post a comment.