In today’s digital age, smartphones have become an integral part of our lives. We use them for communication, entertainment, and to capture important moments in our lives. However, with the convenience of having a camera on our phones, comes the risk of leaked videos from phone or images being shared without our consent. Unfortunately, this has become a common problem in recent years, and the consequences can be devastating. The issue of privacy breach is not limited to celebrities or public figures only, but can happen to anyone. In this article, we will explore the various ways in which videos or images can be leaked from phones, and what steps you can take to protect your privacy.

Images and videos can be leaked from phones? How it is possible.
This question can be divided into two parts: how are photos or videos obtained without consent, and how are they disseminated? In this article, we will explore the various methods used to obtain images and videos without permission, with a particular focus on leaked videos from phones.
#1 Malicious Software
Malicious software, also known as malware, refers to any type of software that is intentionally designed to harm, disrupt, or gain unauthorized access to a computer system or network. Malware can take many forms, including viruses, worms, Trojans, spyware, ransomware, and adware, among others.
Malware can infiltrate a computer system or network in a variety of ways, including through email attachments, infected websites, and software downloads from untrusted sources. Once installed, malware can cause a wide range of problems, from slowing down the computer system to stealing sensitive information such as passwords and credit card numbers.
One of the most common types of malware is a virus, which is a piece of code that can replicate itself and spread from one computer to another. A virus can cause a variety of problems, from deleting files to corrupting the entire operating system. Another common type of malware is spyware, which is designed to collect information about the user’s browsing habits and send it back to the attacker. Spyware can be used to steal sensitive information such as passwords and credit card numbers, as well as to monitor the user’s activities.
Ransomware is another type of malware that has become increasingly common in recent years. Ransomware is designed to encrypt the user’s files and demand payment in exchange for the decryption key. This type of malware can be particularly devastating for businesses, as it can lead to the loss of important data and cause significant financial damage.
To protect against malware, it’s important to keep your software up-to-date with the latest security patches and to use reputable antivirus and anti-malware software. It’s also important to be cautious when downloading software and to only download from trusted sources.
#2 Password Guessing
Another way in which images and videos can be leaked from phones is through password guessing. This occurs when an attacker attempts to guess the user’s password by trying a variety of different combinations. In some cases, the user may have chosen a weak or easily guessable password, such as “1234” or their birthdate. This can make it easier for the attacker to gain access to the phone and any stored files, including images and videos.
In other cases, the attacker may use more advanced techniques such as brute-force attacks, which involve trying every possible combination of characters until the correct password is found. This can be a time-consuming process, but it can be effective if the user’s password is not strong enough.
It’s important to note that attempting to guess someone’s password without their consent is illegal and can result in criminal charges. In addition to being illegal, leaking someone’s phone number or any other personal information without their consent is also a violation of privacy and can cause significant harm to the individual.
To protect against password guessing attacks, it’s important to choose strong and unique passwords that are not easily guessable. This means avoiding common words, phrases, and patterns, and using a combination of letters, numbers, and symbols. It’s also important to use different passwords for different accounts and to change your passwords regularly.
#3 System-Level Attacks
System-level attacks are another way in which images and videos can be leaked from phones. These attacks target the operating system of the phone itself, rather than individual apps or files. System-level attacks can be particularly dangerous because they can give the attacker access to all of the phone’s data, including images and videos.
One way in which system-level attacks can occur is through the use of malicious software, such as a virus or Trojan. Once installed on the phone, this software can take control of the operating system and give the attacker access to all of the phone’s data.
Another way in which system-level attacks can occur is through vulnerabilities in the phone’s operating system. Hackers can exploit these vulnerabilities to gain access to the phone’s data, including images and videos. This is why it’s important to keep your phone’s operating system up-to-date with the latest security patches.
It’s important to note that leaking someone’s phone number or any other personal information without their consent is a serious violation of privacy and can cause significant harm to the individual. There is no legitimate reason to leak someone’s phone number, and doing so can result in criminal charges.
To protect against system-level attacks, it’s important to keep your phone’s operating system up-to-date with the latest security patches. You should also avoid downloading apps from untrusted sources and be cautious when clicking on links or opening email attachments. Finally, it’s important to use strong and unique passwords for your phone and any accounts associated with it.
#4 Social Engineering
Social engineering is a tactic used by attackers to trick people into giving up sensitive information, including images and videos stored on their phones. One common social engineering technique used to obtain cell phone leaks is called phishing. Phishing attacks typically involve sending an email or text message that appears to be from a legitimate source, such as a bank or other trusted institution. The message will often contain a link to a fake website that is designed to look like the real thing, and will ask the user to enter their login credentials or other sensitive information.
Another social engineering technique used to obtain cell phone leaks is called pretexting. Pretexting involves creating a false pretext, or story, in order to trick the victim into giving up sensitive information. For example, an attacker may pretend to be a tech support representative and claim that there is a problem with the victim’s phone that requires access to their data.
To protect against social engineering attacks, it’s important to be cautious when clicking on links or opening email attachments, and to verify the legitimacy of any requests for sensitive information. This can be done by contacting the institution directly using a phone number or email address obtained from a trusted source.
#5 Malicious Acquaintances
Malicious acquaintances can be a significant source of cell phone leaks. These individuals may have access to your phone, either physically or remotely, and share your private images or videos without your consent. This can be motivated by various reasons, such as jealousy, revenge, or even financial gain. In some cases, they may use your private information to extort money from you or others.
If you suspect that someone you know has leaked your photos or videos, it is crucial to take immediate action. You can consider contacting law enforcement authorities and report the incident as a crime. Depending on the situation, the person responsible for the leak may face charges for offenses like cyberbullying, harassment, or even theft.
Alternatively, you can seek the help of a lawyer specializing in privacy and data protection to learn more about your legal rights and options. They can advise you on seeking compensation for any damages or losses you may have suffered due to the leak.
It is also essential to take preventative measures to avoid future cell phone leaks. One way to do this is by setting strong passwords, enabling two-factor authentication, and being cautious about who you share your phone or personal information with. These measures can help reduce the risk of your private images or videos being leaked from your phone by malicious acquaintances.
Images and videos are shared online in various ways
Now that we have explored the different ways photos and videos can be stolen from phones, the next question is how they end up being shared online. While it is not possible to provide an exhaustive list of websites and resources that facilitate this, we can look at the common ways through which leaked videos from phone are shared on the internet. By understanding the underlying mechanisms, you can gain insight into how these images and videos make their way into the public domain.
#1 Peer to Peer
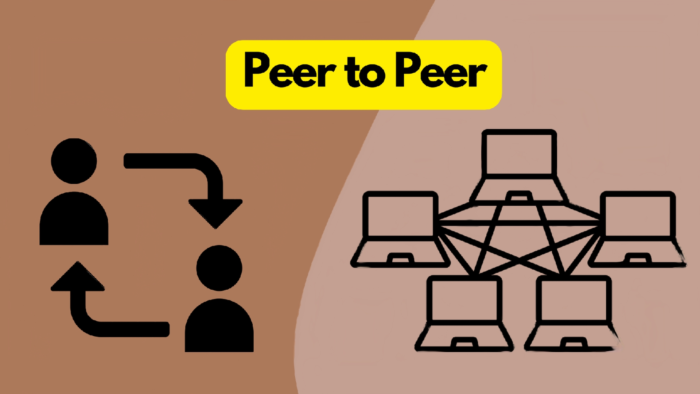
One of the most common ways images and videos are shared online is through peer-to-peer (P2P) networks. These networks allow users to share files directly with each other, without the need for a central server. P2P networks can be used for legitimate purposes, such as sharing large files or distributing software updates. However, they can also be used for illegal activities, such as sharing copyrighted material or distributing illegal content.
P2P networks work by allowing users to connect to each other directly, forming a decentralized network. Each user has their own set of files that they can share with others, and they can also download files from other users on the network. P2P networks are typically used for sharing large files, such as movies, music, or software. However, they can also be used for sharing images and videos.
One of the biggest risks associated with P2P networks is that they can be used to distribute illegal content. For example, some users may use P2P networks to share images and videos that they do not have the rights to distribute, such as copyrighted material or child pornography. This can lead to legal consequences for both the person sharing the content and the person downloading it.
Another risk associated with P2P networks is that they can be used to spread malware. Malicious actors can use P2P networks to distribute malware disguised as legitimate files, such as movies or software updates. When users download these files, they may unknowingly install malware on their computer or mobile device, which can lead to data breaches or other security issues.
#2 The Dark Web

The Dark Web is a hidden part of the internet that is inaccessible through standard search engines or web browsers. It is a place where anonymity is prioritized, and users can browse and share content without being traced. Unfortunately, this anonymity also makes it a haven for illegal activities, including the sharing of illicit images and videos. Due to the encrypted nature of the Dark Web, it is challenging for law enforcement agencies to track down and shut down these illegal activities.
The people who frequent the Dark Web are often involved in criminal activities, and they have little regard for the privacy and well-being of the individuals involved in the images and videos they share. It is crucial to note that accessing the Dark Web and sharing content on it is illegal, and anyone caught doing so could face serious legal consequences. It is important to take steps to protect your personal information and avoid having your images and videos shared on these sites. By avoiding the Dark Web and being mindful of the content you share online, you can protect yourself and prevent your images and videos from being shared without your consent.
#3 Totally Legal Websites
Totally legal websites are also a common way for images and videos to be shared online. These include social media platforms, cloud storage services, and content-sharing websites. While these platforms have terms of service agreements that prohibit the sharing of explicit content, it’s still possible for users to share such content either intentionally or unintentionally.
Social media platforms like Facebook, Twitter, and Instagram have strict community guidelines that prohibit the sharing of explicit content. However, some users may still share this content by creating private groups or accounts, or by sharing it through direct messaging. Cloud storage services like Dropbox and Google Drive are often used to store personal files, but they can also be used to share files with others. While these services have sharing controls that allow users to limit who can view and download their files, files can still be shared if users accidentally or intentionally share the wrong link.
Content-sharing websites like Reddit and Tumblr allow users to share content on a wide range of topics, including explicit content. These sites have moderators who are responsible for enforcing community guidelines, but it’s still possible for inappropriate content to slip through the cracks. Additionally, users can create private subreddits or blogs to share explicit content with select individuals or groups.
Overall, while totally legal websites have measures in place to prevent the sharing of explicit content, it’s still possible for this content to be shared either intentionally or unintentionally. It’s important for users to be aware of the risks associated with sharing sensitive content online and to take appropriate measures to protect their privacy and security.
#4 Social Media
Social media platforms like Facebook, Twitter, and Instagram are among the most popular websites for sharing images and videos. These platforms offer a simple and convenient way to share photos and videos with friends and family. However, social media can also be a breeding ground for image and video leaks, particularly when privacy settings are not configured correctly.
Hackers and malicious individuals may exploit vulnerabilities in social media platforms to gain unauthorized access to private photos and videos. Additionally, some users may inadvertently share private images or videos with the public, either by accident or due to a lack of awareness of the platform’s privacy settings.
One way to protect yourself from image and video leaks on social media is to be mindful of the content you share online. Avoid sharing private or sensitive images and videos, and always review the privacy settings on your social media accounts to ensure that you are not unintentionally sharing content with the public.
It is also important to note that social media platforms have policies in place to address image and video leaks. For example, Facebook allows users to report content that violates its community standards, including photos and videos that contain nudity or sexual activity. Additionally, Instagram has implemented AI-powered tools to proactively detect and remove offensive content.
Frequently Asked Questions
How are videos or images leaked from phones?
Videos or images can be leaked from phones in several ways, including hacking, malware, phishing, social engineering, and malicious acquaintances.
How do hackers steal videos or images from phones?
Hackers can steal videos or images from phones by exploiting vulnerabilities in software or using malware to gain access to the device.
Can malware infect phones and steal videos or images?
Yes, malware can infect phones and steal videos or images, as well as other personal data.
How can I protect my phone from being hacked and my videos or images being leaked?
You can protect your phone by using strong passwords, updating software regularly, avoiding suspicious links or emails, and being cautious when downloading apps.
What should I do if my videos or images have been leaked from my phone?
If your videos or images have been leaked from your phone, you should report the incident to the appropriate authorities and consider consulting a lawyer to explore your legal options.
Can videos or images be leaked from my phone without my knowledge?
Yes, videos or images can be leaked from your phone without your knowledge, especially if you have malware on your device or if someone else has physical access to it.
Are there any totally secure ways to store videos or images on my phone?
While no method is completely foolproof, you can increase your security by using encryption, cloud storage with strong passwords, or dedicated photo or video vault apps that provide an extra layer of protection.





You must be logged in to post a comment.